Data-centric Security: A CDO’s perspective on better data security.
June 21, 2022 | 4 min. read

Data is essential for organizations today, and it is the fuel that drives business. Those who are able to run relevant algorithms and analytics on relevant and readily available data, have a competitive advantage. However, organizations face the challenge of simultaneously streamlining access to valuable data while securing and protecting it. We can meet this challenge by moving to a data-centric security model.
The way we manage and access data today is inefficient. It is messy and chaotic. Organizations have an array of siloed, legacy data systems that are accessed from a variety of platforms. The net result of this system-centric approach to data is a tangled spider web of connections overrun with overlaps and redundancy.
The system-centric approach is unnecessarily complex. It also puts the team or individual protecting the data in the position of gatekeeper. Data security can’t come at the expense of data utility. We want to access and use the data—to get as much value out of the data as possible—which means security needs to be the gate opener rather than the gatekeeper.
How can we improve data security and streamline data access simultaneously? Let’s double-click on that.
Chief Data Officers (CDO) are accountable to create value with data End-to-End, from data management to data activation and outcome-oriented actions. Whether it is our data lake, customer data, product data, or any other kind of data, CDOs are responsible for that data wherever it sits and as it flows through the activity system of an organization and its broader ecosystem.
The goal is to facilitate access to data as effectively and efficiently as possible. A confusing mix of redundant crisscrossing and point-to-point integrations is certainly not efficient and, in a fast paced environment like the one of most businesses, is not effective either because of the lag between when data activation would have the highest value and when the ad hoc integrations make those data actually available for consumption. I would prefer to have all the data in a single content layer where we can easily manage access and reusable integrations through data access policies and APIs.
Someone has responsibility for managing and activating data in an organization, and someone must secure it. Larger companies and mature enterprises have chief information security officers (CISOs)and CDOs. Still, even in smaller or younger organizations, someone fills similar roles regardless of their titles.
Achieving this goal and changing how we manage and protect data requires cooperation and collaboration. Regardless of the exact roles or titles involved, everyone must be rowing in the same direction.
Fortunately, both CISOs and CDOs benefit from shifting to a decoupled data architecture and adopting a data-centric security model. It is easier for the CISO to maintain visibility and manage security when we remove silos, incentivize reusability and reduce complexity. At the same time, simplifying the flow of data helps the CDO minimize the cost and delays of data transfers, data migrations, and data replication that hinder their team from activating data when it’s most valuable.
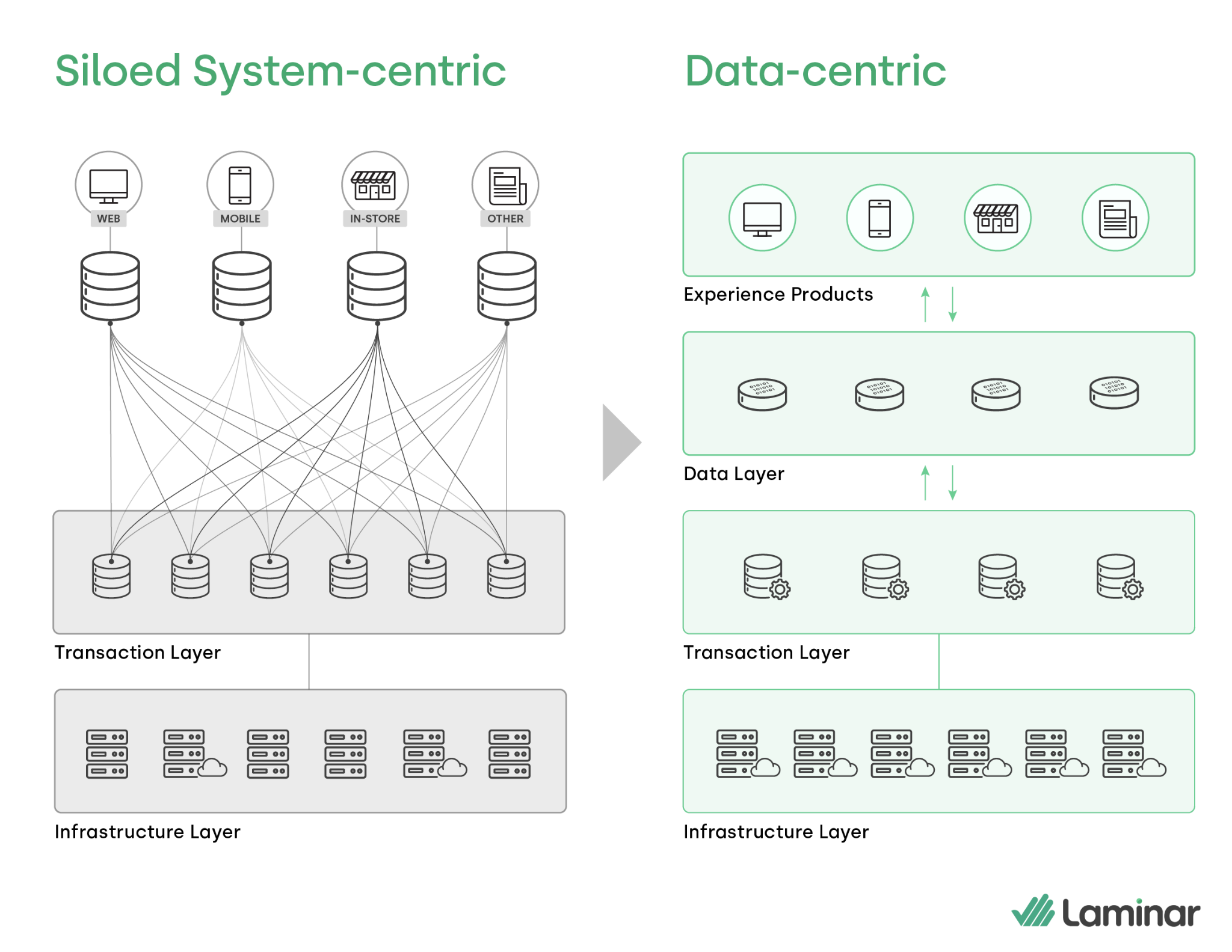
Shifting the approach in this way allows the CISO and CDO to have a shared source of truth—a single platform to define their policies and manage both access and security at the same time. It reduces friction and simplifies the process for everyone involved because as long as policy conditions are met, data access can be granted automatically without sacrificing data security.
The data-centric model also accelerates development. When developers want to introduce a new feature in a system-centric model, they must spend time and effort creating redundant data pipelines. In a data-centric model where data access is managed and enforced through policies, developers can skip that part and focus on the feature itself rather than reinventing the wheel every time.
Achieving this goal is not a matter of simply flipping a switch. There is a lot of inertia behind the legacy model of siloed data systems and the system-centric approach to security. This is a transformation, and it only works if the whole organization gets on board with this operating model.
Ultimately, the data-centric model lets us move from gatekeeper to gate opener. We need to get to a place where everyone behaves with a data layer-first mindset. If we can achieve that state, we can focus on enabling access and extracting value from our data rather than worrying about sprawling data silos and struggling with continuous consolidation efforts to reduce risk and increase efficiency..
Get notified when a new piece is out