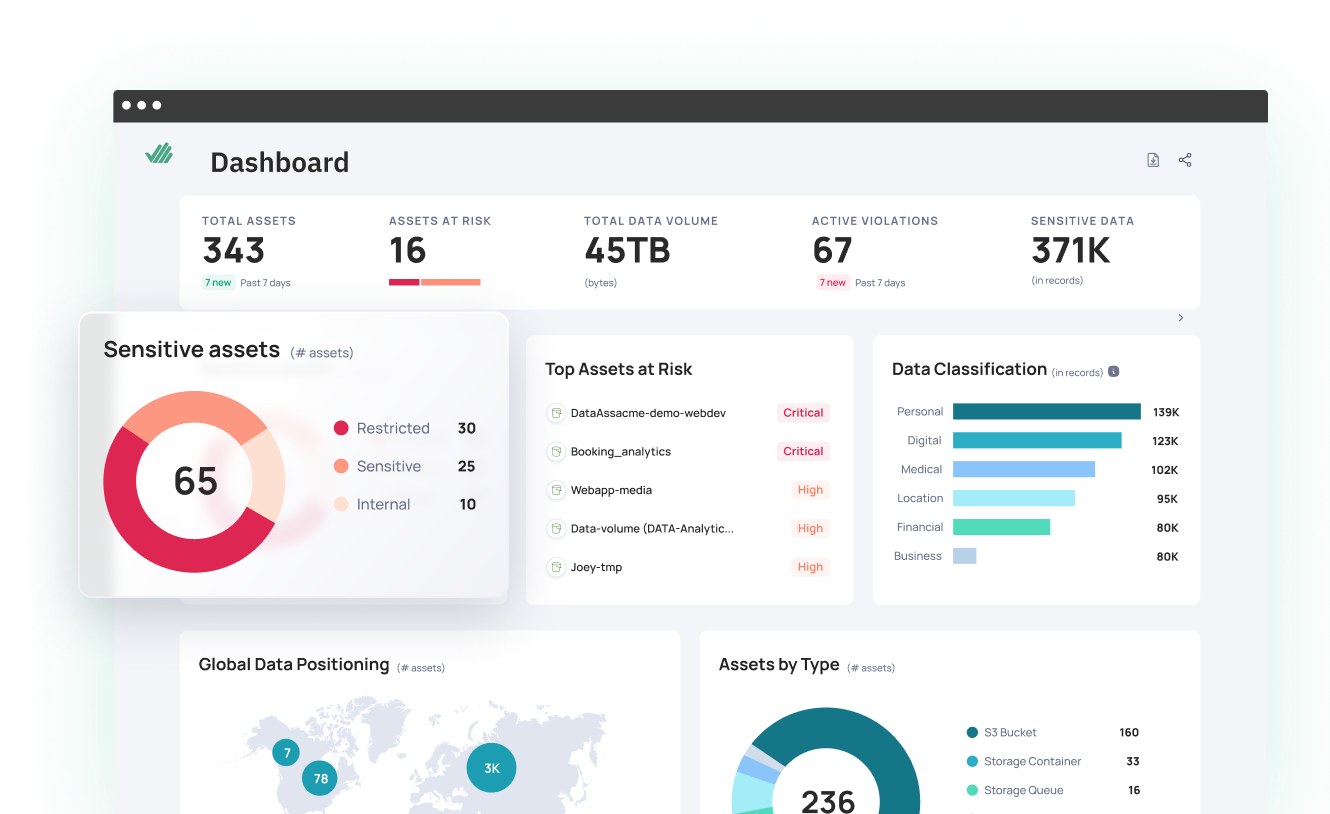
Data Access governance (DAG) Solution
Prevent your next security incident from becoming a data breach
Security incidents are inevitable, but you can minimize their impact by strategically managing access to your organization’s sensitive data – starting with your high-risk identities.
Use Laminar’s Zero Trust data access governance (DAG) capabilities for key data security use cases
Data exfiltration prevention
Insider risk management
Least privilege access
Ransomware risk management
Data breach investigation
Third-party access management
Compliance and regulations
Enforce Zero Trust data security with Laminar’s data access governance solution
Find out who has access to your most sensitive data – whether they are privileged users or not. These are your high-risk identities. Right size their permissions and add extra protections to limit the scope and damage of security incidents.
Discover high-risk identities
Laminar continually assesses your environment to find the highest risk identities – those that would cause the most damage if compromised because of their access to sensitive data.

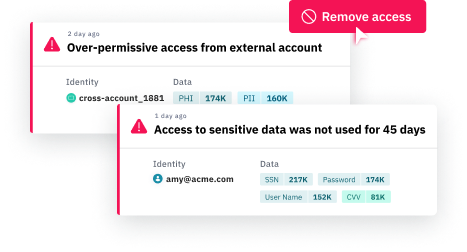
Ensure least privilege access
Reduce the impact of security incidents by ensuring least privilege access to sensitive data. Set guardrails to find and remediate excessive and unused permissions.

Protect high-risk identities
Add an extra layer of defense to high-risk identities. Use Laminar’s real-time monitoring tools, including data detection and response (DDR). Add additional authentication and temporary access.

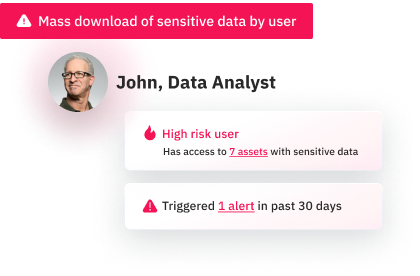
Respond sooner to stop data exfiltration
By focusing your incident response on compromised identities with the most potential damage, you can stop data exfiltration and recover faster.

Prevent your next security incident from becoming a data breach
Feature overview
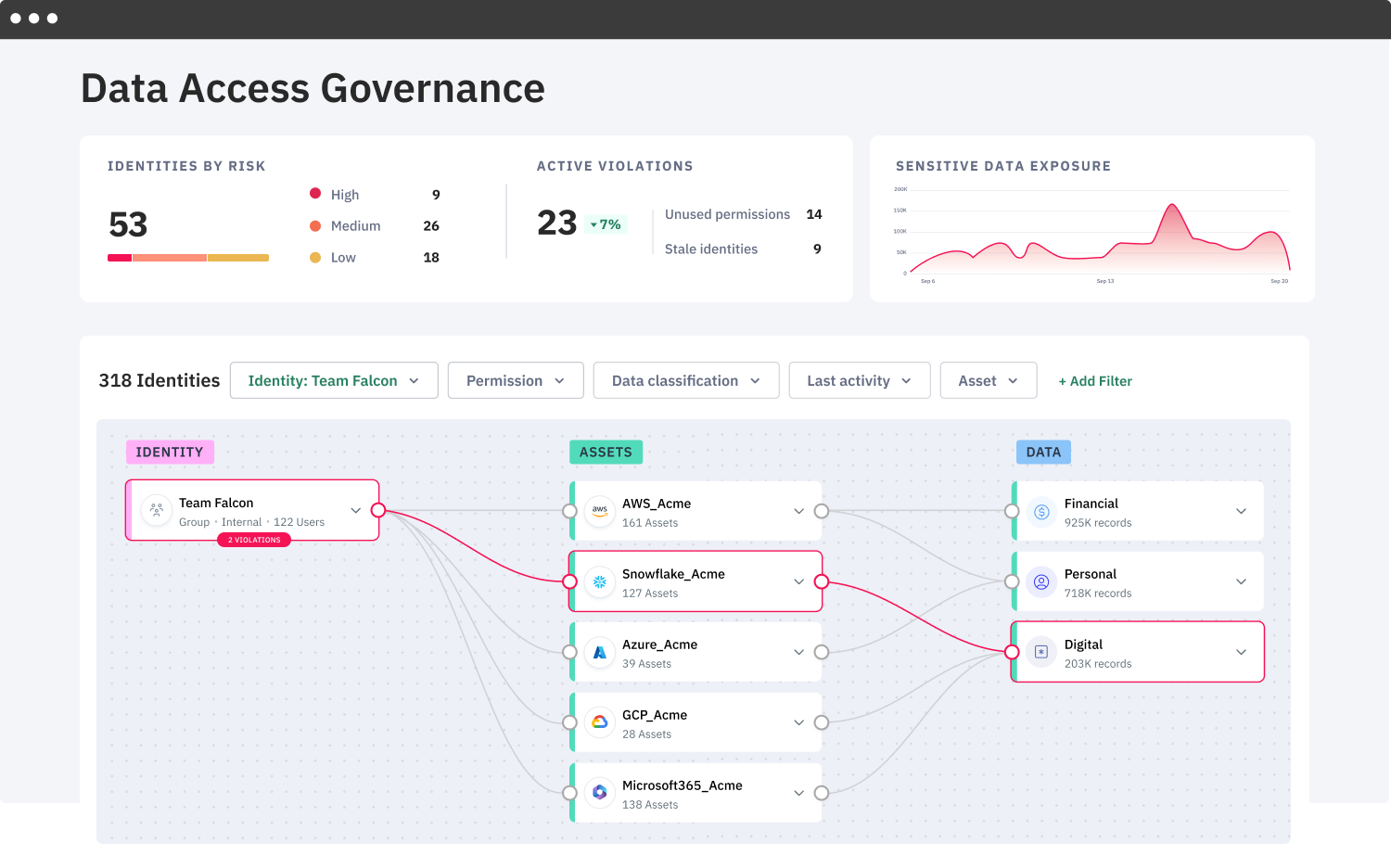
Data access graph
Data access graphs provide quick visibility into who has access to what data, making it easier to review permissions and reduce the attack surface of your sensitive data.
Data-driven risk
assessment
Our AI-powered data classification engine analyzes risk based on data sensitivity, so you can discover high-risk identities and prioritize incident response.
Data access
policies
Ensure compliance by using data access policies to identify and remediate unused, excessive, and misconfigured permissions.
Multi-cloud &
SaaS support
Monitor access to your data wherever it resides across AWS, Azure, GCP, Snowflake, BigQuery, and SaaS.
Continuous, agentless monitoring
Our easy-to-deploy agentless solution continually monitors data access without impacting performance.
Guided remediation & integration
Remediate data access and identity posture violations with guided workflows and integration with identity protection tools.
See Laminar's data security platform in action
Request a personalized demo to see how Laminar can help you.
REQUEST A DEMO