Discover and Control Sensitive Data in Multi-cloud Environments: Use Case Shadow Data
Security teams find the data security attack surface is reduced and visibility is enhanced.
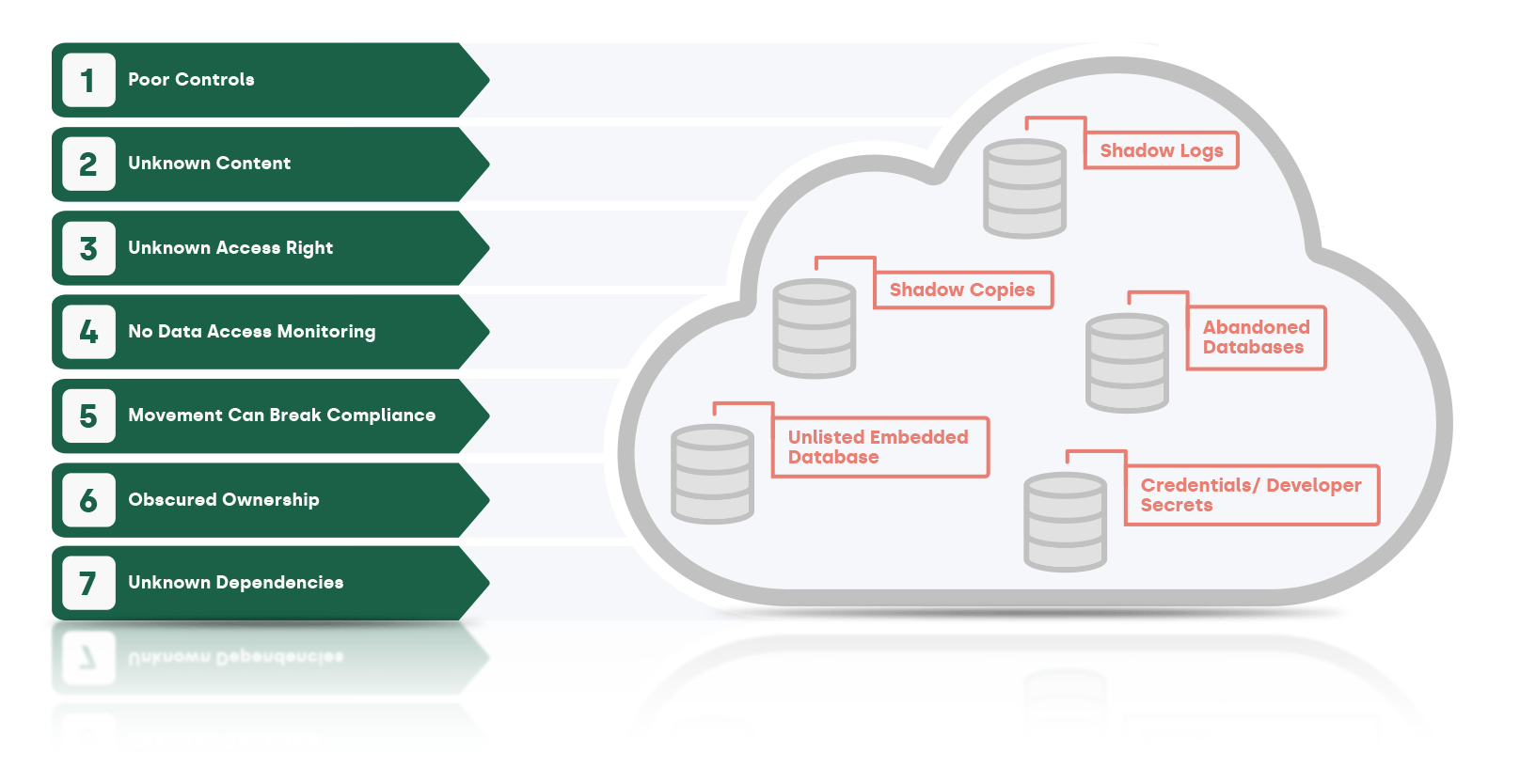
Shadow Data Challenges
While the cloud maximizes flexibility to develop, distribute, backup, and manage all kinds of sensitive data, security teams are facing a deadly combination of a geometrically increased attack surface and near zero visibility, especially of Shadow Data.

Unknown Data Assets
Lacking programmatic discovery of data assets, the full range of data assets is unknown.

Insufficient Controls
Data is often moved outside of the compliance guidelines (across geos) or without copying source controls.

Unclassified Content
The sensitivity of the data types are not discoverable without manual investigation.

Lack of Context
Context such as asset owner, usage, and application dependencies is not known due to turnover or gaps in documentation.

No data access monitoring
Access rights are not known and accesses to data are not monitored much less analyzed for anomalies.

Lack of Detection
Leakage of Shadow Data such as data stores, logs / caches, and credentials / developer secrets is not detected.
Laminar's Shadow Data Solutions
Our cloud data security platform autonomously discovers all Shadow Data in your environment and guides you to remediate or secure it.
How Cloud Data Security Teams Work With Laminar
Laminar’s automation maximizes the efficiency and increases visibility for security teams

Cloud Data Security Teams
With Laminar, Security teams find the data security attack surface is reduced and visibility is enhanced.
- Monitor usage: Monitor real-time cloud data usage and trends even in multi-cloud environments using Laminar’s dashboards.
- Understand data assets: Understand each data asset in detail from the information presented by Laminar in drilldown windows and reports.
- Validate conformance: Ensure that assets are in conformance with security policies.
- Investigate: Investigate prioritized and questionable assets by contacting the owner and the creator of the data.
- Prioritize protections: Ensure that PII, PCI, and other sensitive data receives higher levels of protection.
- Request Action: Request IT or Development take specific actions such as encrypt based on Laminar’s recommendations (manually or via API integrations).
- Respond to Data Leaks in real time: Take action in real time in response to a detected incident (via the organization’s tools or API integrations).
- Remediate: Remediate by taking action such as encryption or quarantine (via the organization’s tools or API integrations).
Benefits Of Cloud Data Security
Provide Defense in Depth for Cloud Data
Provides preventive and detective controls for your data including active defenses and data security attack surface minimization.

Ramp Defenses Incrementally
Data security can be ramped so that “crown jewel” data assets receive the highest levels of protection.

Detect Shadow Data Leaks in Real Time
Detects data leaks and unauthorized infiltrations in real time, even for Shadow Data.

See Laminar’s data security platform in action
Request a personalized demo to see how Laminar can help you.
Request a Demo