What is data detection and response (DDR)?
DDR is a cybersecurity solution that focuses on detecting data-related security threats in real time so security teams can quickly respond to the incident, protect the compromised data, and remediate the data breach – minimizing the financial, regulatory, and reputational impact.
Why do I need data detection and response (DDR)?
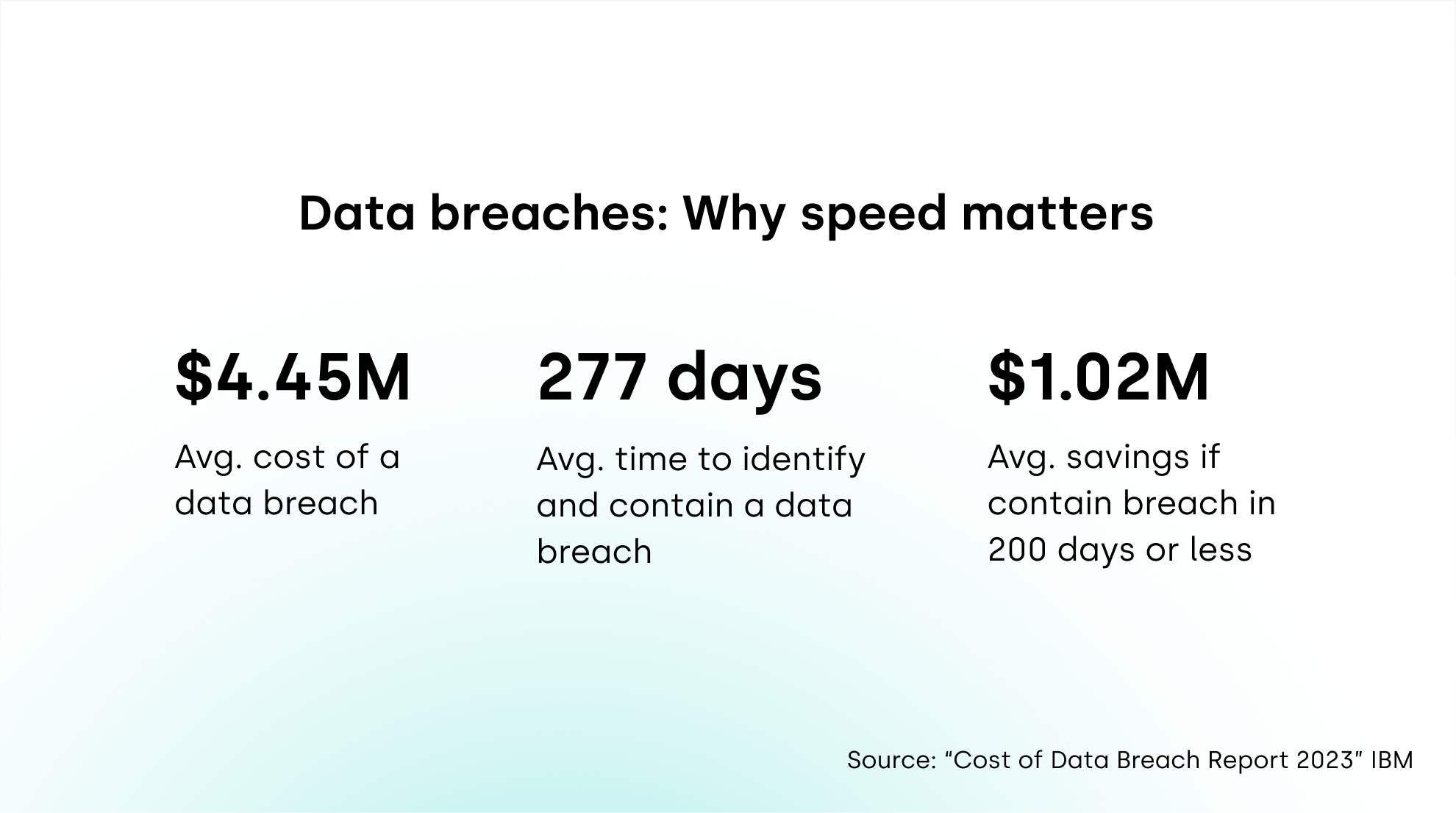
As data breaches have become more common, their impact has also become more costly to organizations. According to IBM’s “Cost of a Data Breach Report 2023,” the average cost of a breach has reached an all-time high of $4.45 million.
Whether the breach is accidental or malicious, the longer an organization’s sensitive data is exposed, the worse the impact. In fact, the average cost difference between breaches that took more than 200 days to find and resolve and those that took less than 200 days is $1.02M.
Why are data breaches so costly?
One of the main costs of a data breach is lost business, which includes revenue loss from business disruptions, system downtime, and customer attrition. According to the IBM Cost of a Data Breach 2023 report, the average cost of lost business due to a data breach is $1.3M.
The high cost of data breaches also stems from regulatory fines. Data breaches can expose sensitive information and personal data, causing companies to inadvertently violate compliance regulations related to data protection, data privacy, and data residency.
Examples of these regulations include the European Union’s General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and California Consumer Privacy Act (CCPA). Violating these regulations can result in significant fines and lead to a loss of trust among customers, investors, and partners, damaging the company’s reputation and potentially impacting its long-term viability. This is especially true when data breaches involve the exposure of customer data such as personally identifiable information (PII), protected health information (PHI), and payment card industry (PCI) data.
DDR can minimize the cost of data breaches by reducing mean time to detect (MTTD) and mean time to respond (MTTR). This allows organizations to contain and remediate threats before any real damage is done – minimizing business disruption and regulatory fines. Having a DDR solution also demonstrates to regulatory authorities that an organization has put into place precautionary measures, which can lower fines. (See for example GDPR criteria for determining fines.)
What are the benefits of data detection and response (DDR)?
While there are many security solutions meant to detect and contain breaches, DDR is focused on monitoring data at its source, which makes it an important cloud data loss prevention (DLP) tool. DDR adds a critical layer of security to IT environments, eliminating blind spots inherent in threat detection solutions that monitor infrastructure, machines, or workloads. DDR works in conjunction with these other solutions.
By employing a DDR solution, organizations can:
- Monitor data wherever it resides or moves – By monitoring activity logs, DDR solutions can monitor data across multi-cloud environments and cloud-based software as a service (SaaS) applications.
- Detect data threats other solutions don’t – DDR monitors data at its source, eliminating blind spots inherent in threat detection solutions focused on infrastructure rather than data. By monitoring how data is used, DDR can detect threats that involve malicious actors accessing data through authorized accounts, which is the case with supply chain attacks and malicious insiders.
- Stop data exfiltration as soon as it occurs – Through real-time or near real-time anomaly detection, DDR can quickly identify unusual data access and behavior indicative of data exfiltration attempts. As soon as data exfiltration is detected, alerts are triggered to notify relevant teams so they can quickly block or isolate the affected systems, preventing data loss and minimizing the impact of the breach. Some DDR solutions trigger automated responses as soon as data exfiltration is detected.
- Investigate breaches more effectively – Investigating a data breach can be a time-consuming and complex process that requires specialized expertise. DDR solutions provide data context, such as what data has been compromised, where it is located, and what entities have accessed the data, allowing security teams to quickly and effectively assess risk, understand blast radius, and determine next steps.
- Minimize costs and reduce alert fatigue – Monitoring all data activity across all cloud assets gets expensive quickly. Plus, it often leads to redundant alerts, causing your team to experience alert fatigue. DDR solutions offer risk-based prioritization and alert customization to reduce costs, prevent alert fatigue, and improve response times.
- Lessen the risk of data regulation violations – Data regulations require organizations to share and govern their data in a way that minimizes risk, often imposing legal consequences and fines when a business fails to meet expectations. DDR solutions help organizations comply with data regulation frameworks by flagging violations as soon as they happen.
How does data detection and response (DDR) work?
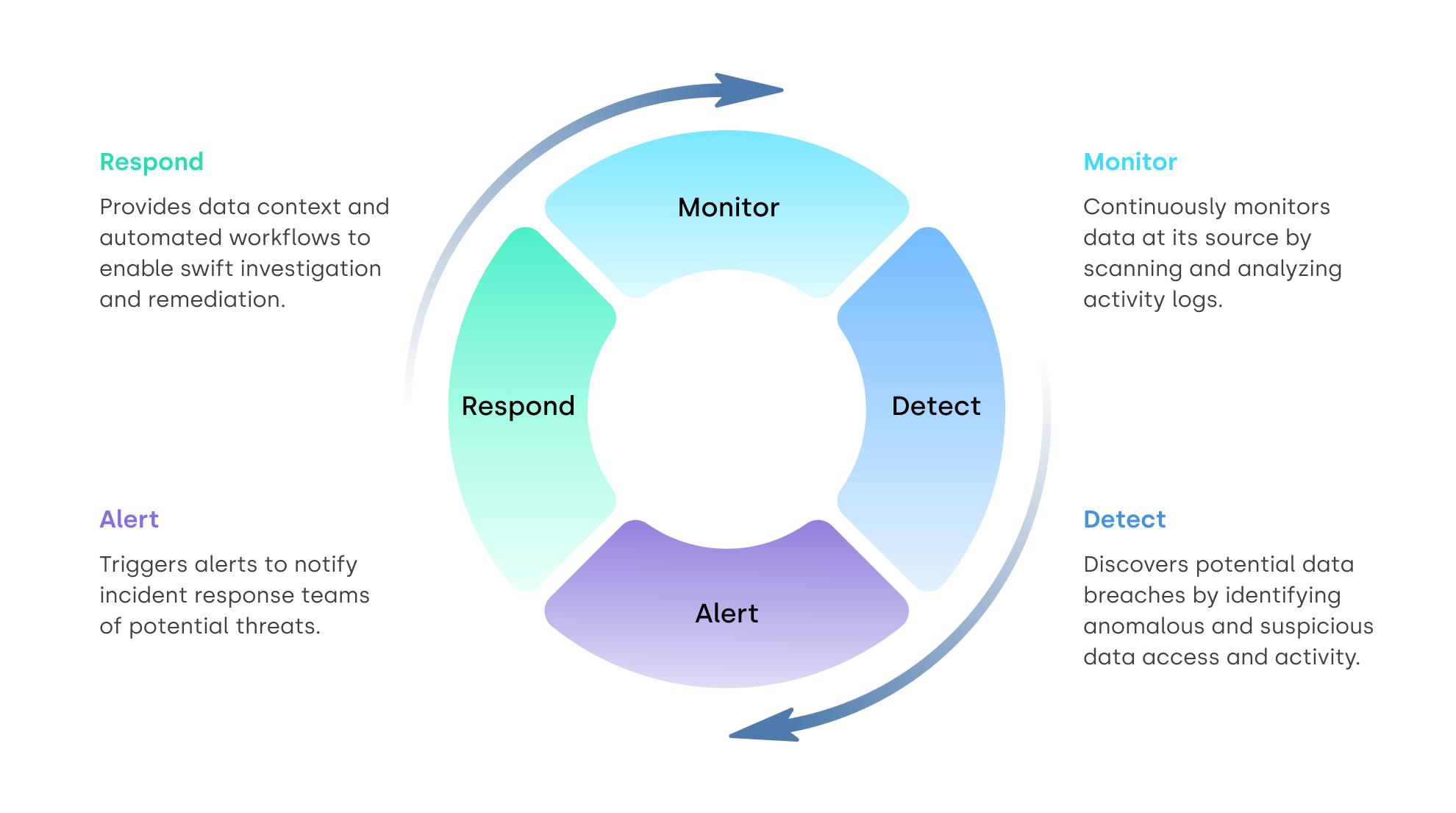
DDR solutions comprise four components: monitoring, detection, alert, and response.
Monitoring involves continuous scanning of data through activity logs such as AWS CloudTrail and Azure Monitor. To keep costs low, DDR solutions can orchestrate activity log monitoring to focus on assets with sensitive data rather than all assets.
Detection refers to the process of identifying anomalous data access and suspicious behavior, which can indicate a data threat. This is done by employing behavior analytics, machine learning, and ongoing research on cyber attack methods.
Examples of anomalies that DDR solutions may detect include:
- Data was accessed from an unusual geo location or IP address
- Logging system was deactivated for an asset with sensitive data
- An abnormally large batch of sensitive data was downloaded, deleted, or modified
- An external entity downloaded sensitive data
- An anonymous entity accessed sensitive data for the first time
Alerts are triggered as soon as a threat is detected, notifying the right teams of the potential data breach. The best DDR tools use data classification to identify sensitive data and send alerts only for threats to assets with sensitive data. This reduces the noise for security operations center (SOC) teams and prevents alert fatigue.
Response is swift and efficient with DDR mechanisms that automate actions to contain and mitigate detected threats, minimizing the potential impact and thwarting further damage. DDR solutions often integrate with security management systems like ITSM (IT service management), SIEM (security information and event management), and SOAR (security orchestration, automation, and response).
What is important to look for in a data detection and response (DDR) solution?
Robust DDR solutions can dramatically reduce the financial, legal, and reputational damage of data breaches by detecting and containing active threats as soon as they occur. When selecting a DDR solution, it is important to look for the following capabilities and features:
- Data context – Comprehensive data context, such as what type of data has been compromised and which entities have accessed that data, allows organizations to accurately assess risk, understand the blast radius, and determine next steps for effective remediation.
- Secure scanning – A secure DDR solution monitors activity logs within an organization’s environment, never exfiltrating data into the solution’s platform.
- Data monitoring at its source – Monitoring data at its source is the only way to guarantee visibility and ensure that no potential threat is left undetected. This eliminates blind spots inherent in threat detection solutions focused on infrastructure rather than data.
- Automated orchestration – DDR solutions that orchestrate the management and monitoring of activity logs to specifically target sensitive data help lower costs and minimize irrelevant alerts by directing resources to what matters most.
- SIEM and SOAR integration – By integrating DDR with other security tools, security teams can expedite incident response and recovery.
- Remediation playbooks – Incident-specific guidance helps security teams contain and remediate data breaches more quickly. This is critical for data loss prevention.
- Wide platform support – Since data moves across environments, it’s beneficial to choose a DDR solution that provides support for multiple cloud service providers (e.g. Amazon Web Services (AWS), Microsoft Azure, and Good Cloud Platform), SaaS applications (e.g. Microsoft 365), data warehouses (e.g. BigQuery and Snowflake), and data store technologies (e.g. object storage (buckets), disks, relational databases, and document databases).
- Seamless deployment and no performance disruption – Agentless solutions are easier to deploy and continually monitor activity logs without impacting performance.
- AI/ML-based threat detection – A DDR solution employing artificial intelligence and machine learning (AI/ML) can leverage these technologies to analyze large volumes of data and identify complex patterns, enabling more accurate and proactive detection of sophisticated and evolving threats.
What is the difference between data detection and response (DDR) and data security posture management (DSPM)?
DDR alerts are notifications generated in response to real-time suspicious activities and data breaches. These alerts prompt immediate action to address active threats. In contrast, DSPM violations refer to instances where an organization’s data security posture fails to comply with predefined security policies or regulatory requirements. DSPM identifies gaps or weaknesses in security controls, providing insights for improvement. While DDR alerts focus on incident response, DSPM violations aim to enhance an organization’s overall data security posture by ensuring compliance and implementing stronger security measures.
What is the difference between data detection and response (DDR) and cloud detection and response (CDR)?
CDR solutions focus on monitoring and securing cloud environments. DDR specializes in monitoring and securing data. DDR detects threats to sensitive data, regardless of its location or format, adding a critical layer of security not possible with solutions that target infrastructure. DDR also allows organizations to focus detection and alerts on their most sensitive data, which minimizes noise, reduces costs, and prevents alert fatigue.
What is the difference between data detection and response (DDR) and other TDIR solutions like EDR and XDR?
Unlike endpoint detection and response (EDR) and extended detection and response (XDR), which primarily focus on threat detection and response at the endpoint level, DDR monitors data wherever it is stored across platforms, mitigating risks associated with data breaches and unauthorized access, regardless of the attack vector or endpoint being targeted.
Another difference is that DDR solutions are often agentless whereas EDR and XDR require agents. DDR is therefore easier to deploy and maintain as it eliminates the need for managing additional software agents on endpoints for installation and ongoing maintenance. Another advantage of agentless solutions is that it has minimal impact on performance, which is usually not the case with agent-based solutions.
How does data detection and response (DDR) fit into a cloud data security platform?
To maximize cloud data protection, organizations should think of their DDR solution as one piece of a holistic data security strategy. This approach should encompass other technologies like data security posture management, data access governance, and compliance management. Together, these solutions can offer end-to-end security for all data.
A complete data security strategy
What is Laminar’s agile data security platform?
Laminar’s agile data security platform offers comprehensive discovery, classification, protection, detection, and response capabilities for multi-cloud environments, SaaS applications, and online file-hosting services. Our agile solution specifically addresses the challenges of securing data in a dynamic, fast-paced cloud environment, where data is constantly proliferating, moving, and changing.
With Laminar, organizations can discover, classify, and proactively safeguard their data – while also monitoring for active threats, assessing risk, and minimizing the impact of any data breaches that may occur.
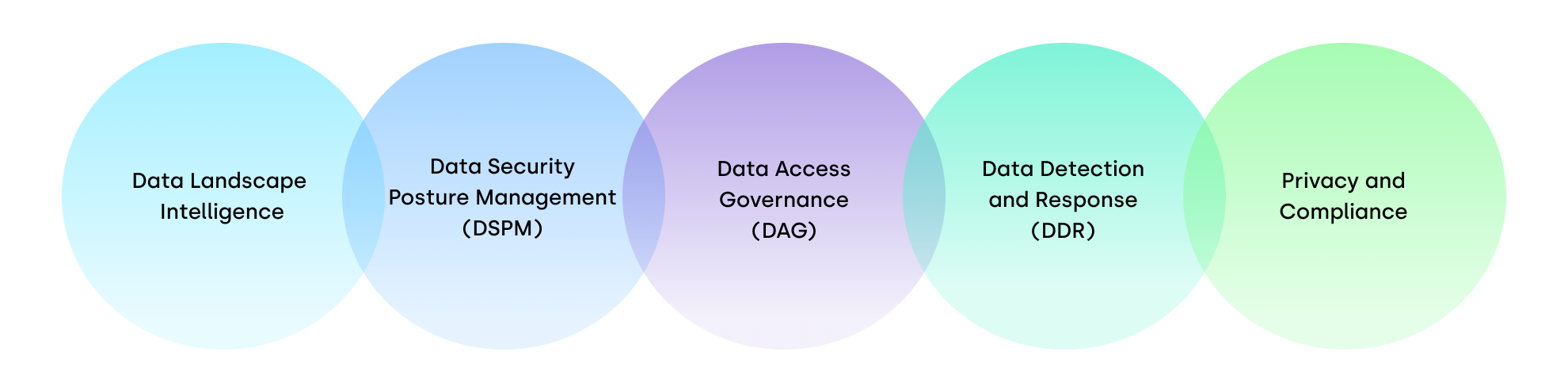
Laminar’s integrated data security platform provides complete data protection:
- Data landscape intelligence – Automatically discovers and classifies all cloud data, so none of it goes unmanaged by security teams.
- Data security posture management (DSPM) – Enforces data policy and applies risk-based prioritization to proactively safeguard sensitive data.
- Data access governance (DAG) – Minimizes blast radius from data leaks by managing user and machine access to sensitive data and upholds a model of least privilege access.
- Data detection and response (DDR) – Detects data breaches as soon as they occur to quickly contain active threats and minimize potential damage.
- Privacy and compliance – Ensure alignment with data regulations and standards, then generates audit-ready compliance reports.
Learn more about Laminar’s data detection and response (DDR) solution and how it fits into the Laminar agile data security platform.



