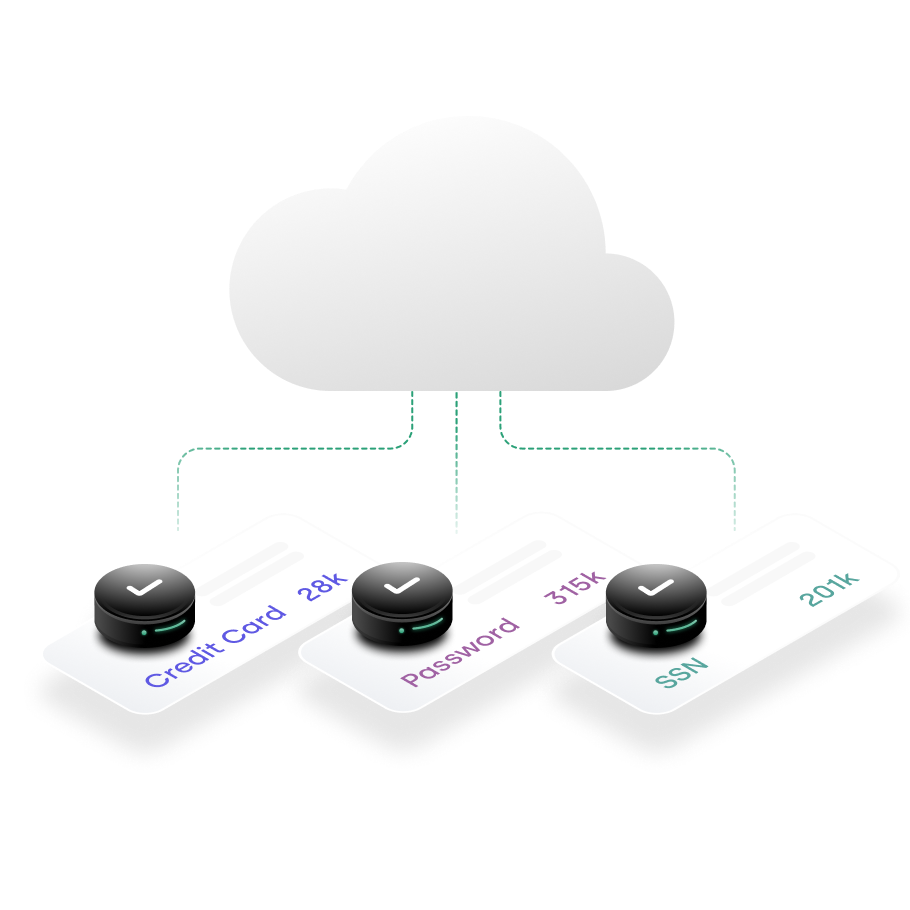
Data transforms your
business. Laminar
secures it.
The first agile data security platform for everything you build and run on AWS, Azure, GCP, Snowflake, BigQuery, and SaaS applications.



Trusted By






Meet urgent data security needs across your organization with one powerful platform
Laminar combines cloud-native design, advanced AI, and cutting-edge research to provide the visibility and control you need to protect your most sensitive data.
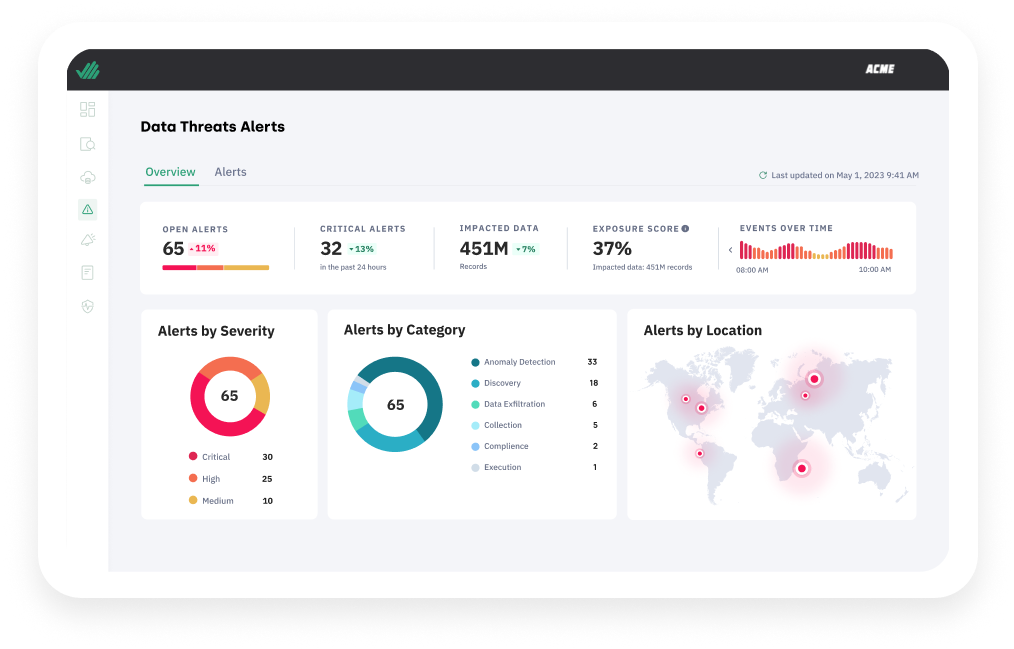
 Data Discovery & Classification
Data Discovery & Classification
View your asset and data inventory with contextual intelligence from autonomous discovery and classification of all your cloud data.
Learn More

 Data Security Posture
Data Security Posture
Management (DSPM)
 Data Access
Data Access
Governance (DAG)

 Data Detection &
Data Detection &
Response (DDR)
 Privacy &
Privacy &
Compliance

I would like to…
-
Discover cloud data
You can’t protect what you can’t see. Seeing all your data, including unknown shadow data, is the first step to securing it. Yet security teams are largely unaware of the growing stream of data sources they’re responsible for. Legacy manual or connector-based approaches are not agile enough for the cloud. What’s needed is the ability to automatically and continuously discover and classify all of your sensitive, proprietary and regulated data: whether structured, unstructured, managed or self-hosted.
-
Prevent public exposure
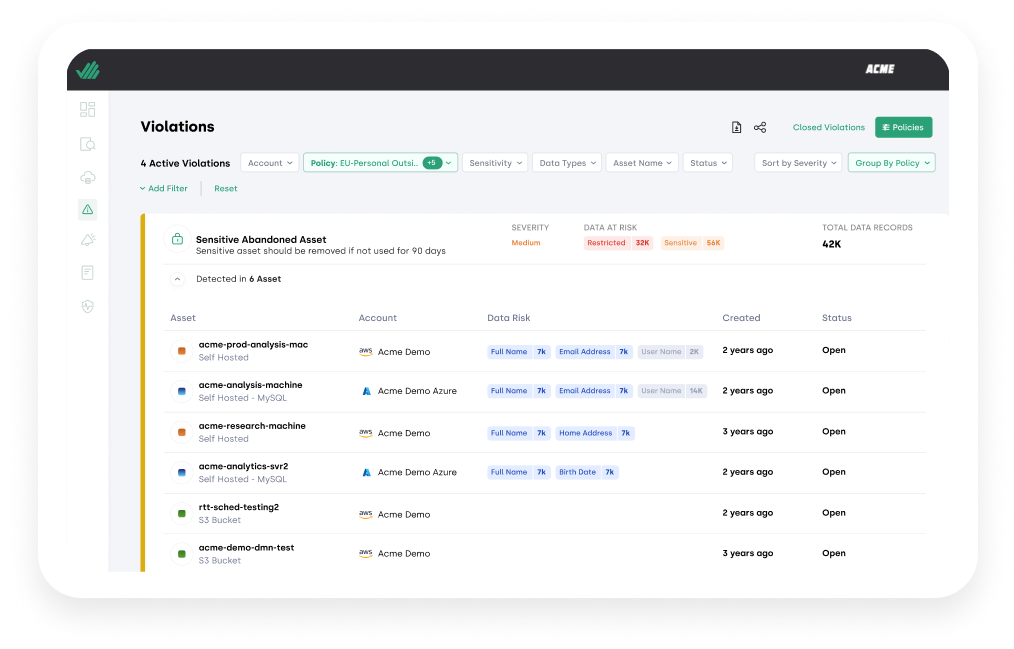
You use public buckets to share data with customers and business partners, but without detailed knowledge of the environment, these convenient data stores often mistakenly get used to store sensitive data. Alternatively, developers might loosen controls or access restrictions for testing purposes, but forget to switch them back afterwards. In either case, assets that contain sensitive ‘shadow data’ can end up being publicly exposed as a result. Fight these potential routes of exposure by continuously pinpointing all exposed, sensitive data and automatically detecting, prioritizing and monitoring exposure violations.
-
Enforce security policy
Your developers and data scientists copy, share and move sensitive data through the cloud each and every day. From an adherence perspective, that makes the data a moving target. Manual methods will no longer suffice. To enforce data security policies you need the ability to automatically and continuously find, prioritize, and fix policy violations for all your cloud data.
-
Secure data handling
Data security frameworks set forth environmental segmentation, encryption or other requirements that are fairly simple to document in policy, but are a nightmare for security teams to enforce. Safeguard your data based on built-in security and compliance frameworks — or create custom policies via guided templates.
-
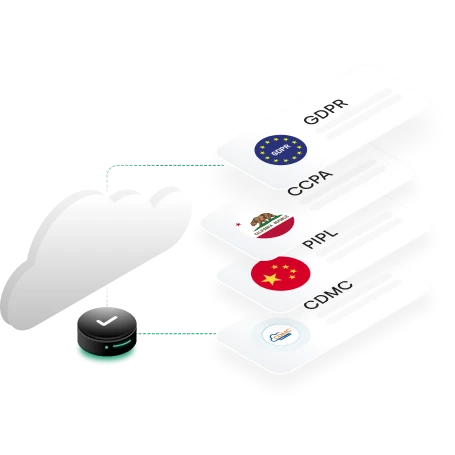
Enforce data sovereignty
Without the right level of visibility into data store geolocations and movement, you can fall foul of data residency requirements —and risk fines and heightened regulatory scrutiny as a result. Receive alerts when sensitive and regulated data violates data residency requirements for CPRA, GDPR, and more.
-
Meet GRC requirements
Staying ahead of data privacy and governance requirements as set forth by internal and external privacy and governance stakeholders is no easy feat. You have to codify policy requirements, monitor for compliance, and then collect evidence to prove that compliance. Manual efforts simply can’t keep up. It’s time to find a solution that streamlines evidence collection for internal and external privacy and governance stakeholders, via autonomous data discovery and classification, and continuously enforce compliance.
Re-imagining data security for the cloud
EXPERIENCE THE BENEFITSFast time-to-value
Find sensitive data assets and uncover risk almost immediately. You can implement Laminar in hours and present comprehensive findings within a week.
Empower value creators
Empower your developers and data scientists to innovate freely while protecting the company. Laminar’s automated policy enforcement alerts you to any data policy violations without limiting speed and flexibility.
Reduce cloud
costs
Stop paying storage fees for unknown and unused data. Continuously find all abandoned, orphaned and redundant data, with all the context you need to understand if deletion is the right decision.
Improve security
outcomes
Eliminate countless hours spent installing and maintaining agents/connectors and sifting through hundreds of low-risk alerts and instead focus on strategic data security, compliance, and governance initiatives/programs.
Turn your team into
data security experts
Enhance the effectiveness of your data security and privacy personnel —whatever their level of experience — with Laminar’s combination of richness and simplicity.
What security leaders are saying
about Laminar

"Laminar gives my team confidence around the location of our data assets. It supports our discovery objectives, and is an essential part of our data security program."

Yaniv Toledano
VP, Global CISO & IT, Pagaya

"Laminar gives us visibility into what data we have and where it sits, regardless of what kind of asset it’s stored in. This allows us to create and enforce policies to secure our sensitive data more effectively and to turn on logging only where necessary."

Tony Carella
Head of Security, Shakepay

"Laminar empowers our team and equips us with the right tool to remediate issues quickly and efficiently."

Guy Fridman
Head of Security Operations and Response. Booking Holdings

"Laminar’s product is great, it gives us visibility to know where our sensitive data is and where it’s exposed."

Gregor Siwinski
Chief Technology Officer, Payability
Laminar by the numbers
B+
SENSITIVE DATA RECORDS DISCOVERED
M+
AVERAGE SHADOW DATA RECORDS PER CUSTOMER
PB+
VOLUME OF DATA SCANNED
K+
DATA ASSETS PROTECTED
See Laminar’s cloud-native platform in action
Request a personalized demo to see how Laminar can help you.