Power your cybersecurity strategy with an integrated data security framework
November 9, 2023 | 10 min. read

Malicious actors came out swinging at the start of 2023, and they aren’t slowing down any time soon. Data breaches increased by 156% between Q1 and Q2 alone. The numbers speak for themselves: today’s approach to data security isn’t working.
Take MGM Resorts and Caesars Entertainment as examples. These multi-billion dollar companies were both victims of recent ransomware attacks. Caesars’ ransom payout was in the ballpark of $30 million. MGM chose not to pay the ransomware-as-a-service organization, leaving their systems down for ten days and causing continued slowdowns for hotel guests in the following weeks.
Today’s data security strategies need new solutions, but unfortunately, many existing tools can only manage one piece of that much bigger and more complex puzzle. Businesses need a holistic data security solution that thoroughly covers every component of a comprehensive data security framework.
But how do you know if a vendor is really all it’s cracked up to be?
We recommend using an integrated data security framework that supports the various elements of cybersecurity. An industry-accepted framework can serve as a litmus test to ensure that your chosen platform covers the most critical facets of data security and keeps bad actors at bay.
Modern data security is incredibly complicated due to vast amounts of dynamic data, complex multi-cloud and hybrid ecosystems, rapidly evolving threats, and stringent regulatory requirements. It’s a lot to juggle—especially since security, governance, privacy, and data roles often share the various responsibilities related to data security.
That’s why organizations should start with a holistic data security framework to make sense of (and solve) these requirements and regulations. Applicable frameworks come from a collective of experts who pooled their knowledge and real-world experiences to create a set of tried-and-true principles. Countless organizations have also tested these principles by applying them in real-life data security scenarios.
You can use a holistic data security framework to:
Here at Laminar, our data security framework of choice is the National Institute of Standards and Technology (NIST) Cybersecurity Framework Version 1.1. We believe it encompasses the most critical aspects of modern data security. This framework is the most widely adopted in the U.S., as the U.S. Department of Commerce developed it. It’s also versatile enough to support most data security efforts—regardless of industry or location.
The NIST Framework breaks the most important aspects of data security into five functions:
Upon its release in early 2024, NIST 2.0 will also add a Govern function, further tying together security, privacy, and governance priorities.
Organizations should note that NIST did not intend for each function to operate as individual steps in a process. Instead, each of them should serve as continuous and concurrent initiatives.
In addition, NIST does not take a narrow, siloed approach to data security posture management (DSPM), data access governance (DAG) or data detection and response (DDR). Rather, the framework considers the whole picture, recognizing that data security is an ongoing, interwoven discipline. This big-picture view creates the continuity organizations need to protect their data effectively, and solutions will hopefully follow this lead.
A complete data security platform should mirror this principle of big-picture continuity. Read on to see how a widely accepted data security framework (NIST, in this case) and an integrated security platform go hand in hand.
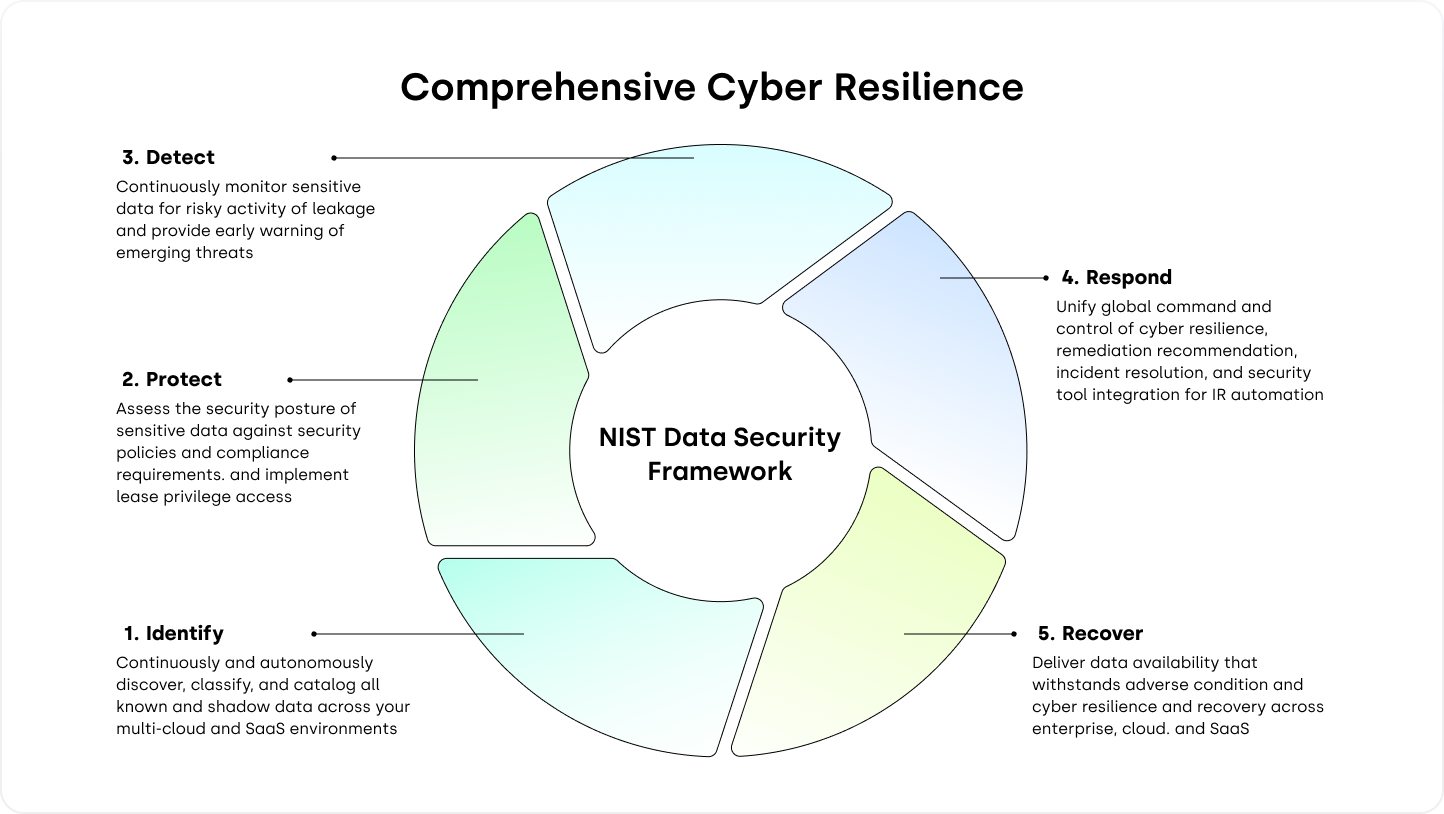
The NIST framework states that a data security program begins with identifying where your data lives, how it flows, and where it could be vulnerable. This function is all about getting a bird’s eye view of your entire data landscape. The data discovery process should also include inventorying all shadow data outside the bounds of known data stores.
However, today’s complex multi-cloud and hybrid ecosystems often make data discovery and classification challenging. Manual processes can’t keep up with the pace of data, and legacy solutions often need to be manually connected—taking up lots of time, effort, and resources.
At Laminar, we recommend using Data Landscape Intelligence to streamline and centralize the discovery and classification process.
Data Landscape Intelligence is all about gathering information on which data you have and the context around it. It supports data security efforts by determining each data store’s risk level based on location, adjacent assets, and level of access permitted to personnel.
To facilitate this process without hindering productivity, Data Landscape Intelligence goes beyond using manual processes. Finding and inventorying all data manually takes far too much time in a fast-moving cloud environment. Instead, organizations should rely on autonomous, continuous discovery and classification of all known and unknown cloud data, and compile findings in an always up-to-date data inventory.
Essential data security platform capabilities for identifying data include:
Data security posture management (DSPM) is a vital piece to the Protect function. A DSPM solution pulls together all the information gathered through a data discovery and classification solution, along with information collected throughout the other functions of the framework. It then uses this information to determine the security posture of your sensitive data while continuously scanning your environment for any changes.
Protecting your data in an ephemeral cloud environment also takes the proper level of access control and monitoring capabilities. To monitor their environments, many organizations turn to Data Access Governance (DAG): setting rules for who can access your data. DAG reduces data exposure and minimizes the blast radius from data leaks by controlling user (application) and machine access to sensitive data.
DAG employs the least privilege principle, ensuring that only authorized roles and third-party applications can access an organization’s sensitive data. DAG tools will also continuously monitor who and what accesses data, flagging unauthorized access or suspicious behavior.
Essential data security platform capabilities for protecting data include:
The Detect function of the NIST framework focuses on monitoring the environment for anomalous activity that might indicate an emerging threat. Many organizations rely on a Data Detection and Response (DDR) solution to facilitate this level of vigilance. DDR automatically finds and alerts on any irregular activity that could point to a threat, such as a new unknown login, data exfiltration, or a suspicious permission change. This information about real-time activities enables teams to detect active threats and minimize potential damage quickly.
Essential data security platform capabilities for detecting data threats include:
The next function of the NIST framework, Respond, is about communicating all suspicious activity to the proper staff members to make remediation as efficient and straightforward as possible. Many data security platforms can respond to irregular events by automatically removing access privileges or triggering de-identification (data auto-masking/encryption).
However, some security incidents require human intervention. In these cases, your chosen data security platforms should be able to communicate in a relevant and timely manner, empowering the right people to investigate the incident and take corrective action quickly. It should also integrate with alerting and workflow automation tools, such as ticketing solutions.
Your data security platform should use threat intelligence and forensics features to fine-tune information and deliver the proper context to the right teams in near real-time. To enable these features, the platform must be able to interface with numerous logs, data security policies, and other monitoring platforms—drawing context from and working with all intelligence sources to holistically protect your data.
Essential data security platform capabilities for responding to data threats include:
Despite the protections that data security teams put in place, we live in a threat landscape where attackers are continually innovating as well, so it’s only a question of when, not if, a breach will occur. When breaches do happen, bringing data back into the proper environments can be incredibly difficult. Even backups often include the malware that initially put the data at risk. As a result, when reinstating the data, teams might accidentally reinstate the attack malware as well.
Many organizations rely on a data recovery solution to quickly recover business-critical data in the event of an attack—without re-introducing the malware that caused the issue in the first place. As such, these recovery solutions must provide visibility into where and how the attack began and which exact data stores are at risk.
A data recovery platform can help your team get back to normal after an attack with quick recovery of the latest clean (that is, not infected with malware) data in several different situations. It’s also a good idea to institute proactive recovery testing, ensuring that your apps are prepared for a smooth data recovery process before an incident even happens.
Essential data security platform capabilities for recovering from data threats include:
An all-in-one complete data security platform that meets the needs of all five functions of the NIST framework can make a holistic—and, most importantly, effective—data security approach possible. Laminar and Rubrik have come together to provide the industry’s first complete data security platform that fulfills all five NIST functions across enterprise, SaaS, and hybrid multi-cloud environments.
Executing all five of these functions at once can be overwhelming, especially when data security teams might lack the proper in-house support. Implementing NIST recommendations entirely on your own can cause gaps in your data security approach and create too many human dependencies—bottlenecking productivity and leading to errors. It takes powerful automation, seamless integrations, and a holistic view of your data landscape to succeed.
Laminar’s agile data security focuses on maintaining the security of your data with powerful identification, protection, and detection functions, while Rubrik Security Cloud focuses on responding to active incidents and safely recovering data.
Learn more about how our comprehensive data security platform secures the world’s data.
Get notified when a new piece is out