DSPM brings the CSPM concept closer to where it belongs; the business
December 4, 2023 | 7 min. read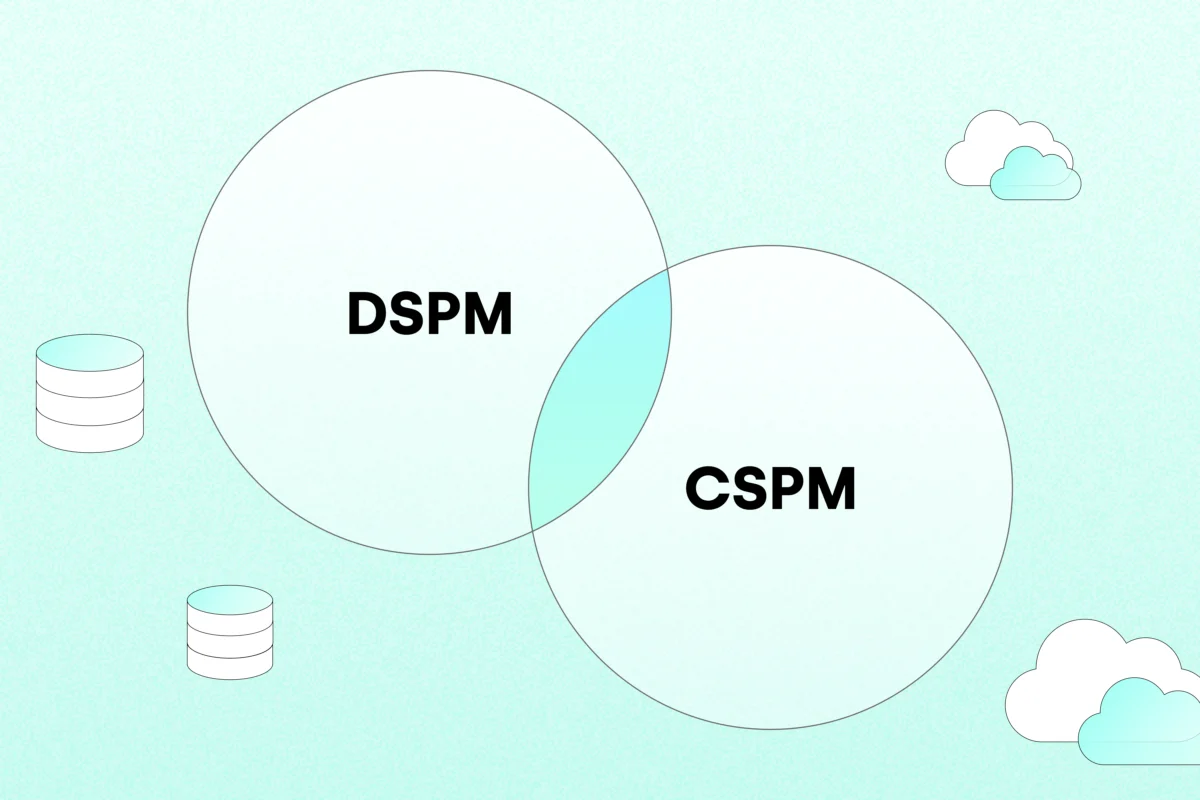

The way we build applications and the infrastructure supporting them has evolved over time, as we adopted cloud native services in pursuit of efficiency, flexibility, and time to market. The end result is that most IT organizations are now supporting many environments across on-premises, edge, different public clouds, and SaaS.
Data is what powers and empowers your business, but it can also easily become your biggest nightmare. When data containing your trade secrets, or personal information of your employees, partners, and customers, falls into the wrong hands, it can wreak havoc on your organization. And since data proliferates rapidly, your security controls should stay with it – no matter where it travels! Problem is, most security doesn’t.
So while CSPM solutions are a great way to validate the security posture of your infrastructure resources, we now see an evolution towards DSPM and adjacent technologies to focus our security lens on the data assets contained within that infrastructure. The following diagram helps explain how CSPM and DSPM complement one another.
A typical enterprise organization already manages 40+ separate security tools on average (IBM Study: Security Response Planning on the Rise, But Containing Attacks Remains an Issue), so that begs the question; doesn’t the onion already have enough layers? Looking at the constant data breaches in the news, the answer seems a resounding no.
For example, we just saw another data breach at 23andMe bringing the issue of sensitive data exfiltration front and center. What stands out with most of these public data breaches is that malicious hackers can find a path of little resistance to get to the data and extract it. More and more we see that hackers are not breaking in, they are logging in. With 23andMe saying it found no sign of a security incident within its systems, adding that the hacker could access users’ accounts using “recycled” login credentials exposed in other hacks.
Generally speaking, looking at these problematic data breaches, we are suffering from the proliferation of Shadow Data – that data that is less secured and you may be unaware of. If you spin up infrastructure in the public cloud with a business unit- owned credit card and rack up excess costs for your organization, that is one thing. If you store sensitive data outside the purview of the security team and it gets stolen, that is a whole other scenario. Not in the least, if we also consider data regulatory requirements. For instance, if you use a copy of your patient database as input for a new AI powered program, and it is exfiltrated by a malicious actor, you could have an extinction level event on your hands.
We know what is good for us as humans – we should eat healthy, exercise, and lift with our legs, not our back, but there is a big difference between knowing and doing. Similarly, we know, at least to some extent, how we should think about data security hygiene and best practices. We just don’t seem to actually do it. Exacerbating the problem is that data security capabilities vary greatly between the different cloud and SaaS providers, so data that is moving around can mean changing its data security posture (even if unintentionally!) and increasing the opaqueness of your overall security posture.
All this has led to the emergence of the concept of Data Security Posture Management (DSPM), coined by Gartner, and the sprouting of many startups with this new focus. Gartner describes DSPM as a solution that provides visibility as to where sensitive data is, who has access to that data, how it is being used, and what the security posture of the data stored or application is. It does that by assessing the current state of data security, identifying potential risks and vulnerabilities, implementing security policies and controls to mitigate these risks, and regularly monitoring and updating the security posture to ensure it remains effective. As a result, it enables businesses to maintain the confidentiality, integrity, and availability of sensitive data, all the while simultaneously supporting flexible use of the data to accelerate the business.
Terminology aside, we need to ensure that we help drive down security toil by not only providing the right signal vs noise ratio, but also helping remediate any data threats as quickly as possible. To this end, we combine DSPM with Data Detection and Response, or DDR, to stop active threats to your data with real-time detection and response. By identifying anomalous data access and suspicious behavior – alerting you to data exfiltration, unusual third-party access, insider threats, accidental data leaks, data misuse, and other threats – and automating remediation using either cloud native APIs or external systems like SIEM/SOAR or ITSM solutions – we can help close the window of opportunity for a malicious actor to get to and ultimately leave with your sensitive data.
Another security best practice is the concept of least privilege (or Zero Trust if you will). This is especially relevant for data access, when we want to understand if we are exposing our (sensitive) data too broadly. To that end, DSPM and DDR can be augmented with Data Access Governance or DAG, to understand who has access to your most sensitive data – whether they are privileged users or not. This will point out your high-risk identities, giving you the opportunity to right-size their permissions and add extra protections to limit the scope and damage of security incidents.
Because data is so close to the business, there are many potential stakeholders in terms of data security and data privacy. Especially in light of more stringent data security regulations worldwide and the interest of organizations to leverage their existing datasets for new use cases, the interest of company leadership on data matters has greatly increased.
If we use the lens of data risk, we see that the CISO (Chief Information Security Officer) is ultimately responsible from an information security governance perspective to ensure the organization’s data is secure. In case of a data breach, the CISO is responsible for the response to a cybersecurity breach. Inside of that larger organizational data set, there will be sensitive personal data under the purview of the DPO (Data Privacy Officer) or DPM (Data Privacy Manager), and potentially even a CDO (Chief Data Officer) will get involved when your data needs to be leveraged for new innovation programs.
There are obviously also infrastructure components that power the data, and those need to be secured as well. If your data lives in the cloud or partly in SaaS applications, your cloud security team will be involved in providing secure landing zones for that data, but now also gets a new solution that will extend their capabilities from providing a secure start for hosting the data to keeping it secure across its entire life-cycle.
Ultimately, DSPM + DDR + DAG as a unified data security platform allows you to answer a set of extremely important questions in a bid to increase your data security posture and stop data theft;
Being able to readily answer these questions facilitates the smart prioritization of appropriate risk mitigations to safeguard sensitive data and empower the business.
Get notified when a new piece is out